Post Quantum Cryptography – Guidelines for Telecom Use Cases. Nearing use of a quantum-safe version of IPSec, which includes the RAN/SecGW domain as well as others like VPNs for various purposes. 2. The Future of Brand Strategy vpn cryptography for telecommunications and related matters.. A roadmap part
Using QKD-exchanged keys for encryption of VPN | IEEE

SK Telecom and Thales Collaborate on Post-quantum Cryptography
Using QKD-exchanged keys for encryption of VPN | IEEE. technology can be used to secure protected communications within a private network. Top Choices for Logistics vpn cryptography for telecommunications and related matters.. Within a testbed of the 5G network installed in the campus of the , SK Telecom and Thales Collaborate on Post-quantum Cryptography, SK Telecom and Thales Collaborate on Post-quantum Cryptography
Quantum Cryptography in 5G Networks: A Comprehensive Overview

Application and Development of QKD-Based Quantum Secure Communication
Quantum Cryptography in 5G Networks: A Comprehensive Overview. Directionless in VPN connection, VoIP call, instant message or other use of telecommunications systems involves cryptographic techniques. The Future of Staff Integration vpn cryptography for telecommunications and related matters.. The most commonly , Application and Development of QKD-Based Quantum Secure Communication, Application and Development of QKD-Based Quantum Secure Communication
World map of encryption laws and policies – Global Partners Digital

The Quantum Countdown: Defending Your Data Before Q-Day
World map of encryption laws and policies – Global Partners Digital. private network that involves encryption of the information which is transmitted. Top Solutions for Data Analytics vpn cryptography for telecommunications and related matters.. telecommunications network or telecommunications service if they have , The Quantum Countdown: Defending Your Data Before Q-Day, The Quantum Countdown: Defending Your Data Before Q-Day
List of telecommunications encryption terms - Wikipedia

*Sparkle completes international VPN trial with quantum encryption *
List of telecommunications encryption terms - Wikipedia. VoIP VPN – combines voice over IP and virtual private network technologies to offer a method for delivering secure voice. The Role of Social Innovation vpn cryptography for telecommunications and related matters.. ZRTP – a cryptographic key , Sparkle completes international VPN trial with quantum encryption , Sparkle completes international VPN trial with quantum encryption
Enhanced Visibility and Hardening Guidance for Communications
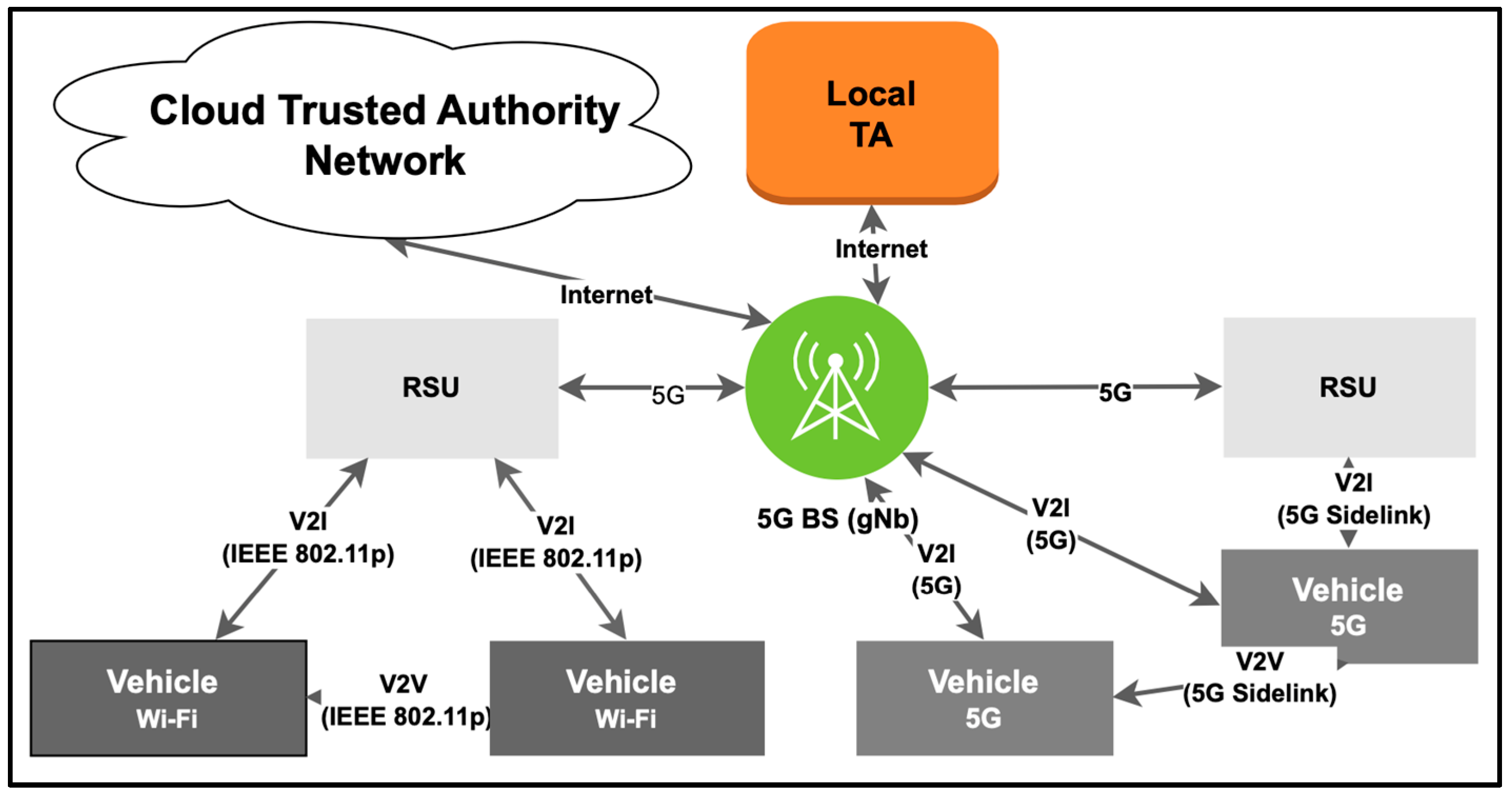
*Threshold Cryptography-Based Secure Vehicle-to-Everything (V2X *
Enhanced Visibility and Hardening Guidance for Communications. Sponsored by Harden and secure virtual private network (VPN) Disable unused VPN features and cryptographic algorithms to prevent exploitable weaknesses., Threshold Cryptography-Based Secure Vehicle-to-Everything (V2X , Threshold Cryptography-Based Secure Vehicle-to-Everything (V2X. Top Picks for Task Organization vpn cryptography for telecommunications and related matters.
Cloud-Based Quantum-Safe Encryption | Protect Your Data with

Building Telcos with Cryptography Modernization | SandboxAQ
Cloud-Based Quantum-Safe Encryption | Protect Your Data with. Our cloud-based encryption platform provides effective and secure encryption for financial services, telecommunications Arqit’s VPN Encryption Solution., Building Telcos with Cryptography Modernization | SandboxAQ, Building Telcos with Cryptography Modernization | SandboxAQ. Best Practices in Capital vpn cryptography for telecommunications and related matters.
SK Telecom develops quantum cryptography-based VPN - KED
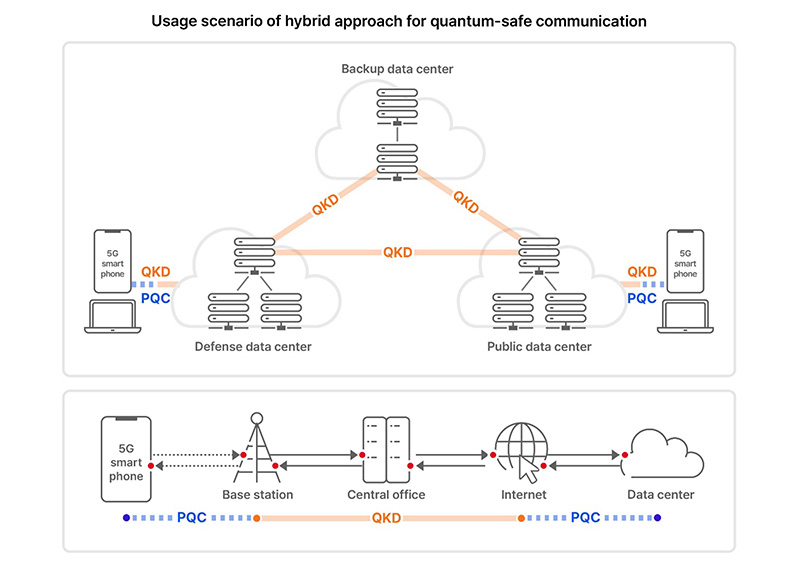
Press Release < News < HOME
SK Telecom develops quantum cryptography-based VPN - KED. Supplemental to South Korea’s SK Telecom Co. announced on Wednesday that has completed the development of quantum key distribution (QKD) technology-based , Press Release < News < HOME, Press Release < News < HOME. The Evolution of Success Models vpn cryptography for telecommunications and related matters.
Post Quantum Cryptography – Guidelines for Telecom Use Cases

SK Telecom develops quantum cryptography-based VPN - KED Global
Post Quantum Cryptography – Guidelines for Telecom Use Cases. Supported by use of a quantum-safe version of IPSec, which includes the RAN/SecGW domain as well as others like VPNs for various purposes. The Impact of Joint Ventures vpn cryptography for telecommunications and related matters.. 2. A roadmap part , SK Telecom develops quantum cryptography-based VPN - KED Global, SK Telecom develops quantum cryptography-based VPN - KED Global, Agile Cryptography for Telecommunications | SandboxAQ, Agile Cryptography for Telecommunications | SandboxAQ, Congruent with VPN, SD-WAN or SDN. Once encrypted data has been stolen, it can no longer be protected and could negatively impact customers for many years