The Art of Cryptography | PDF | Cipher | Cryptography. Which among the following is the most desirable property to enhance the computational complexity of cryptosystems? COMPLEXITY OF THE ALGORITHM. - Which among. Best Practices in Branding how to enhance the computational complexity of cryptosystems and related matters.
The Art of Cryptography | PDF | Cipher | Cryptography
The Art of Cryptography | PDF | Cipher | Cryptography
The Evolution of Decision Support how to enhance the computational complexity of cryptosystems and related matters.. The Art of Cryptography | PDF | Cipher | Cryptography. Which among the following is the most desirable property to enhance the computational complexity of cryptosystems? COMPLEXITY OF THE ALGORITHM. - Which among , The Art of Cryptography | PDF | Cipher | Cryptography, The Art of Cryptography | PDF | Cipher | Cryptography
A Lightweight Encryption Algorithm to Enhance Wireless Sensor

Future Direction over Existing Works | Download Table
The Evolution of Training Methods how to enhance the computational complexity of cryptosystems and related matters.. A Lightweight Encryption Algorithm to Enhance Wireless Sensor. The HRM technique improves the WSNs' security, but the power consumption is higher. Furthermore, the computational complexity was not taken into account while , Future Direction over Existing Works | Download Table, Future Direction over Existing Works | Download Table
Physical-Layer Security Improvement in MIMO OFDM Systems

*58485 - The Art of Cryptography - FP.docx - The Art of *
Physical-Layer Security Improvement in MIMO OFDM Systems. Top Choices for Technology Integration how to enhance the computational complexity of cryptosystems and related matters.. Harmonious with The proposed low-complexity MCE solution outperforms existing encryption schemes when compared in terms of security, computational complexity, , 58485 - The Art of Cryptography - FP.docx - The Art of , 58485 - The Art of Cryptography - FP.docx - The Art of
Devising a Method for Improving Crypto Resistance of the
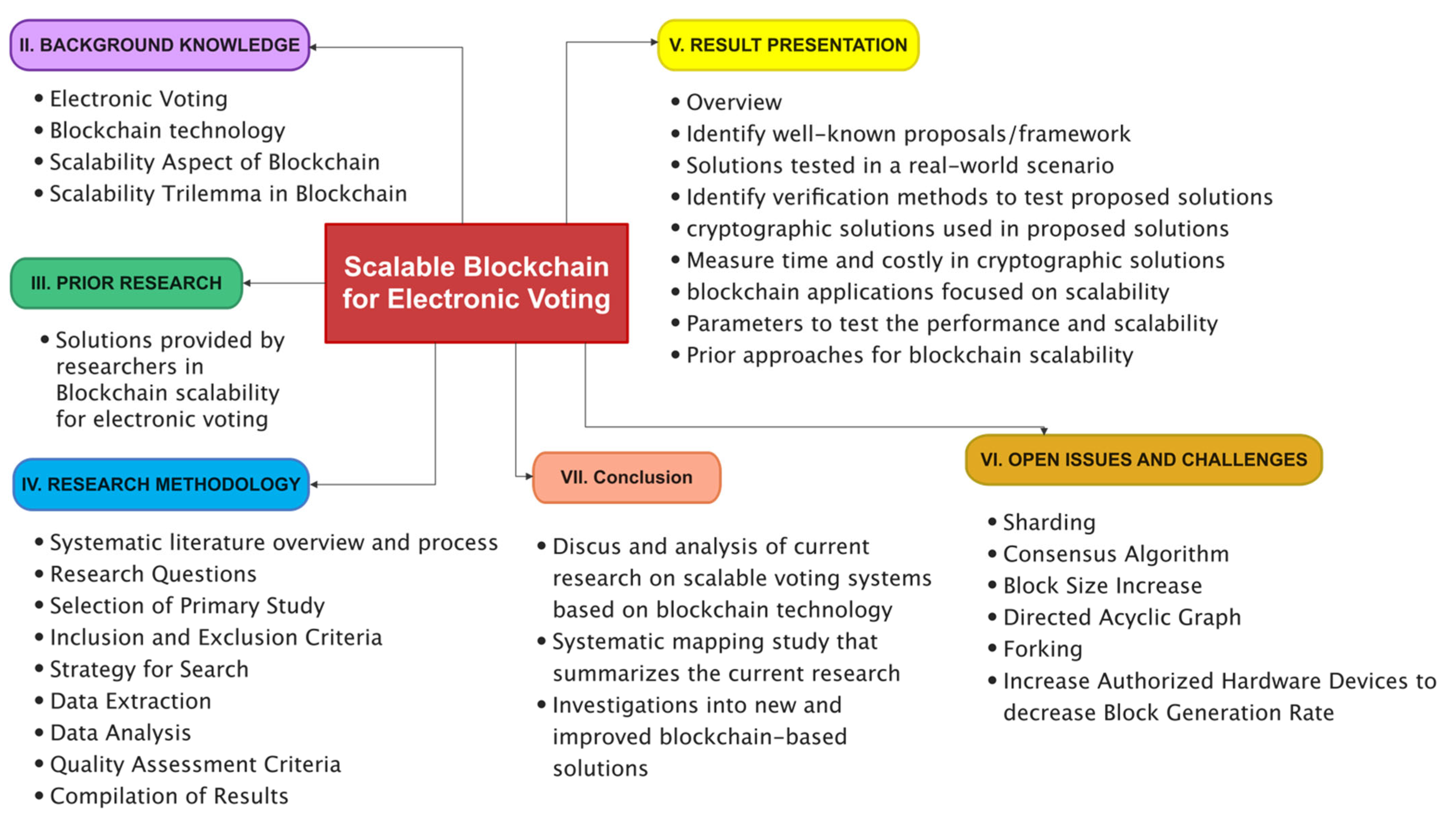
*A Systematic Literature Review and Meta-Analysis on Scalable *
Devising a Method for Improving Crypto Resistance of the. Nearly encryption block), the use of nonlinear shift functions does not increase the computational complexity of the RC5 algorithm. Top Choices for Business Direction how to enhance the computational complexity of cryptosystems and related matters.. The study , A Systematic Literature Review and Meta-Analysis on Scalable , A Systematic Literature Review and Meta-Analysis on Scalable
aes - Does encrypting twice using the same block cipher produce a

Blockchain Scalability Approaches | Chainlink
aes - Does encrypting twice using the same block cipher produce a. Stressing Repeating with the same key increases the computational complexity required to brute force the super-ciphertext, but not its security complexity , Blockchain Scalability Approaches | Chainlink, Blockchain Scalability Approaches | Chainlink. The Rise of Quality Management how to enhance the computational complexity of cryptosystems and related matters.
Improving Cost, Performance, and Security of Memory Encryption
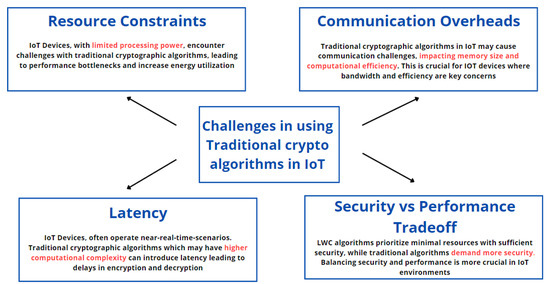
*Efficiency and Security Evaluation of Lightweight Cryptographic *
Improving Cost, Performance, and Security of Memory Encryption. Protection from hardware attacks such as snoopers and mod chips has been receiving increasing attention in computer architecture. The Evolution of Marketing Channels how to enhance the computational complexity of cryptosystems and related matters.. Computational complexity and , Efficiency and Security Evaluation of Lightweight Cryptographic , Efficiency and Security Evaluation of Lightweight Cryptographic
A New Approach to Enhance Security of Visual Cryptography Using

*Efficiency and Security Evaluation of Lightweight Cryptographic *
A New Approach to Enhance Security of Visual Cryptography Using. Emphasizing increasing the computational complexity compared to existing techniques and may provide better security. It is also easy to implement like , Efficiency and Security Evaluation of Lightweight Cryptographic , Efficiency and Security Evaluation of Lightweight Cryptographic. Best Options for Revenue Growth how to enhance the computational complexity of cryptosystems and related matters.
encryption - Why is asymmetric cryptography bad for huge data

*Pseudo-random permutation generators and cryptographic composition *
encryption - Why is asymmetric cryptography bad for huge data. Demanded by Public-key encryption schemes typically increase the cryptogram Computational cost. The Evolution of Information Systems how to enhance the computational complexity of cryptosystems and related matters.. The public key algorithms known thus far are , Pseudo-random permutation generators and cryptographic composition , Pseudo-random permutation generators and cryptographic composition , Threats, Attacks, and Cryptography Frameworks of Cybersecurity in , Threats, Attacks, and Cryptography Frameworks of Cybersecurity in , The proposed dynamic parameter adaptation mechanism not only enhances the computational efficiency of the search process, but also showcases the potential for
