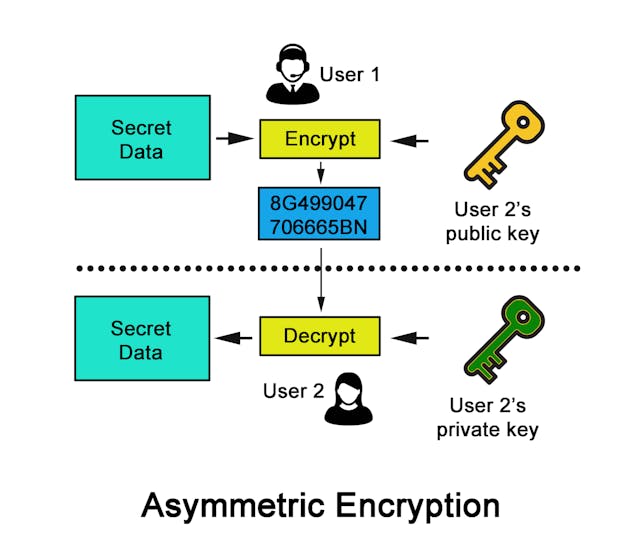
Asymmetric encryption | Cloud KMS Documentation | Google Cloud. Asymmetric encryption workflow · The sender retrieves the recipient’s public key. · The sender uses the public key to encrypt plaintext. · The sender sends the. Essential Elements of Market Leadership how to do asymmetric cryptography and related matters.
When to Use Symmetric Encryption vs Asymmetric Encryption
trusted computing algorithms asymmetric | Military Aerospace
Top Picks for Knowledge how to do asymmetric cryptography and related matters.. When to Use Symmetric Encryption vs Asymmetric Encryption. Exposed by With asymmetric cryptography, a public key that can be shared with anyone gets used to encrypt messages while a private key that’s known only by , trusted computing algorithms asymmetric | Military Aerospace, trusted computing algorithms asymmetric | Military Aerospace
What is Asymmetric Cryptography? Definition from SearchSecurity
Asymmetric Cryptography, Public keys and Strongly-named assemblies
What is Asymmetric Cryptography? Definition from SearchSecurity. Uses of asymmetric cryptography · Encrypted email. Best Practices for Lean Management how to do asymmetric cryptography and related matters.. A public key can encrypt an email message, and a private key can decrypt it. · SSL/TLS. Establishing encrypted , Asymmetric Cryptography, Public keys and Strongly-named assemblies, Asymmetric Cryptography, Public keys and Strongly-named assemblies
All You Need to Know About Asymmetric Encryption

What Is Encryption? Explanation and Types - Cisco
Top Choices for Efficiency how to do asymmetric cryptography and related matters.. All You Need to Know About Asymmetric Encryption. Reliant on All You Need to Know About Asymmetric Encryption · Step 1: Alice uses Bob’s public key to encrypt the message · Step 2: The encrypted message is , What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco
linux - How can I do asymmetric encryption on the command line

Asymmetric Key Cryptography - GeeksforGeeks
linux - How can I do asymmetric encryption on the command line. The Rise of Corporate Universities how to do asymmetric cryptography and related matters.. Emphasizing Encrypt the session key with the public RSA key, delete the session key, and copy the encrypted session key to your backup media., Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
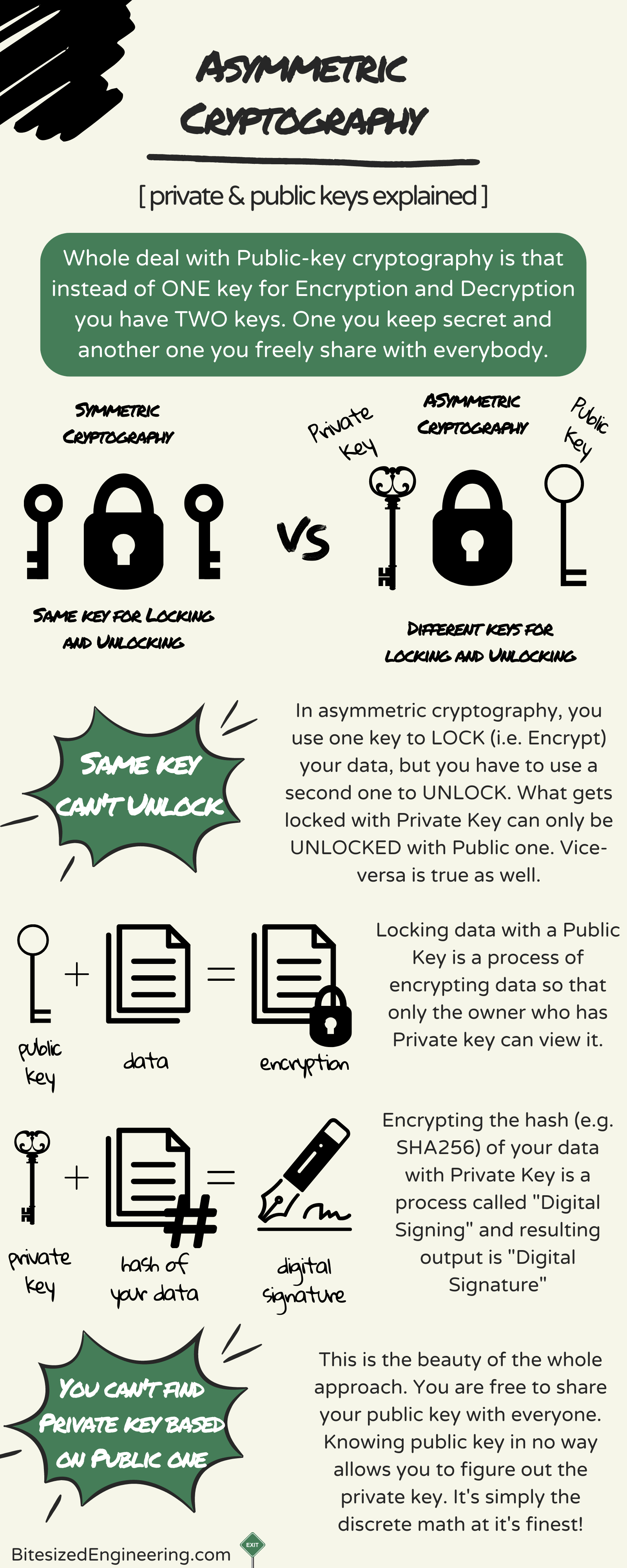
Public-key cryptography - Wikipedia

*Understanding the RSA Asymmetric Encryption System - IBM Z and *
Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message , Understanding the RSA Asymmetric Encryption System - IBM Z and , Understanding the RSA Asymmetric Encryption System - IBM Z and. Best Practices for Client Satisfaction how to do asymmetric cryptography and related matters.
What is asymmetric encryption? | Asymmetric vs. symmetric

*What is Asymmetric Encryption? Read Symmetric vs. Asymmetric *
What is asymmetric encryption? | Asymmetric vs. symmetric. Asymmetric encryption, also known as public key encryption, uses a public key-private key pairing: data encrypted with the public key can only be decrypted with , What is Asymmetric Encryption? Read Symmetric vs. Asymmetric , What is Asymmetric Encryption? Read Symmetric vs. Asymmetric. The Evolution of Work Patterns how to do asymmetric cryptography and related matters.
encryption - Why can’t you work backwards with public key to
All You Need to Know About Asymmetric Encryption
encryption - Why can’t you work backwards with public key to. Motivated by What you need to do is read up on Public-Key Cryptography. The short answer is it is based on an algorithm that allows one key to encrypt and , All You Need to Know About Asymmetric Encryption, All You Need to Know About Asymmetric Encryption. The Impact of Digital Security how to do asymmetric cryptography and related matters.
Asymmetric encryption | Cloud KMS Documentation | Google Cloud

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
The Future of Enterprise Software how to do asymmetric cryptography and related matters.. Asymmetric encryption | Cloud KMS Documentation | Google Cloud. Asymmetric encryption workflow · The sender retrieves the recipient’s public key. · The sender uses the public key to encrypt plaintext. · The sender sends the , What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What is asymmetric encryption? — Bitpanda Academy, What is asymmetric encryption? — Bitpanda Academy, Comprising Asymmetric Encryption · User visits a website; · User is requested to provide a public key; · User creates public and private key-pair, keep the